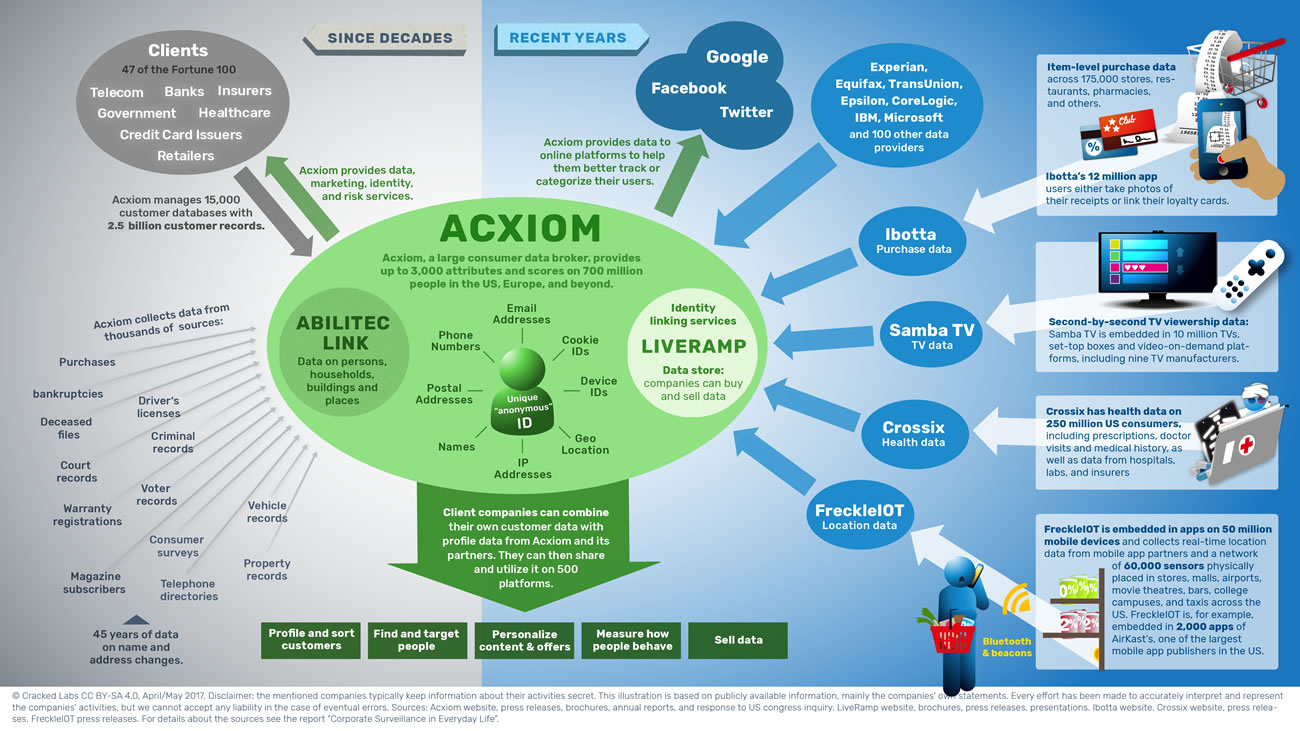
In the digital age, the collection and sale of personal details have become a cornerstone of the online economy. This section delves into the less visible aspects of this industry, exploring how these practices can lead to significant privacy concerns and ethical dilemmas. While the convenience of tailored advertisements and services might seem appealing, the underlying mechanisms often come with hidden costs.
Information intermediaries, often operating in the shadows, play a crucial role in this ecosystem. They compile vast amounts of personal information, which is then packaged and sold to various entities. This process, while legal, raises serious questions about consent and the right to privacy. The implications extend beyond mere annoyance; they can lead to more profound issues such as identity theft and targeted manipulation.
Understanding the Mechanisms
To grasp the full extent of the problem, it’s essential to understand the mechanisms through which these intermediaries operate. They utilize sophisticated algorithms to sift through public and private databases, gathering details that range from shopping habits to social media activity. This information is then analyzed and used to create detailed profiles of individuals, which are sold to marketers, political campaigns, and even law enforcement agencies.
The Ethical Quandary
The ethical implications of these practices are profound. Individuals often remain unaware of the extent to which their personal information is being collected and utilized. This lack of transparency not only violates privacy but also undermines trust in digital platforms. As we continue to navigate this complex landscape, it becomes crucial to address these issues head-on, advocating for greater accountability and transparency in the information aggregation industry.
Understanding Information Intermediaries
This section delves into how information intermediaries systematically encroach upon individual privacy through their operational frameworks. It explores the inherent design features that facilitate this invasion, highlighting the mechanisms and consequences of such practices.
Information intermediaries, often operating behind the scenes, collect and manage vast amounts of personal information. Their business models are predicated on the acquisition and sale of this information, which inherently involves a degree of privacy infringement. Here are key aspects of how privacy is compromised by design:
- Collection Methods: Intermediaries gather personal details through various channels, including online browsing habits, purchase histories, and social media interactions. These methods are often automated and pervasive, capturing more information than necessary.
- Storage and Security: The storage of collected information is typically centralized, making it a prime target for cyber-attacks. Despite advancements in security technology, the sheer volume and sensitivity of the data make it difficult to protect adequately.
- Use of Information: The information collected is not only used for targeted advertising but also for more intrusive purposes such as profiling and behavioral analysis. This use extends beyond the original intent of data collection, often without explicit consent from the individuals involved.
- Transparency and Control: There is a significant lack of transparency in how intermediaries use personal information. Users often have limited control over their data, with complex and buried privacy settings that are difficult to navigate.
The systematic invasion of privacy by these intermediaries raises serious ethical and legal questions. It underscores the need for robust regulatory frameworks and technological solutions to protect individual rights and ensure that the use of personal information is both ethical and lawful.
Privacy Invasion by Design
This section delves into the systematic encroachment on individual confidentiality, orchestrated through the strategic collection and utilization of personal information. It explores how entities gather sensitive details with the explicit intent of leveraging them for commercial or manipulative purposes, often without the knowledge or consent of the individuals involved.
The mechanism of information gathering is intricately designed to be covert, ensuring that users remain unaware of the extent of their exposure. This practice not only infringes on personal privacy but also sets a dangerous precedent for the normalization of surveillance in everyday life.
| Method | Purpose | Impact |
|---|---|---|
| Surveillance Technology | Monitoring user behavior | Increased vulnerability to targeted marketing |
| Data Mining | Extracting personal patterns | Potential for identity manipulation |
| Social Media Scrutiny | Analyzing public profiles | Exposure of private life details |
The implications of such invasions extend beyond mere privacy concerns. They encompass a broader spectrum of risks, including financial exploitation, social profiling, and even political influence. The continuous accumulation of personal data creates a digital footprint that is susceptible to misuse, highlighting the urgent need for stringent regulations and consumer awareness.
Financial Gain Through Data Trafficking
This section delves into how entities involved in the trade of personal information leverage this sensitive material for substantial monetary benefits. By understanding the mechanisms and motivations behind these practices, we can better comprehend the broader implications on privacy and security.
The lucrative nature of information trafficking is driven by several key factors:
- High Demand: There is a constant demand for personal details in various sectors, including marketing, finance, and politics. This demand fuels the market for purchased information.
- Lack of Regulation: In many regions, the trade of personal data operates with minimal oversight, allowing participants to operate with relative impunity.
- Scalability: Once a method of gathering or selling information is established, it can be scaled up almost infinitely, leading to significant profits with minimal additional investment.
The financial incentives behind information trafficking are further amplified by:
- Targeted Advertising: Companies use purchased personal details to create highly targeted advertising campaigns, which can significantly increase conversion rates and profitability.
- Credit Scoring and Financial Services: Personal information is crucial for assessing creditworthiness and tailoring financial products, providing a direct pathway to financial gain for those trafficking such information.
- Political Campaigning: Politicians and parties utilize detailed personal profiles to craft messages that resonate with specific demographics, enhancing their campaign strategies and potentially swaying election outcomes.
The consequences of these practices extend beyond financial gains, impacting individual privacy rights and societal trust in digital platforms. Addressing these issues requires a multifaceted approach, including stricter regulations, enhanced consumer awareness, and technological solutions designed to protect personal information.
Political Manipulation via Personal Data

Political influence has taken a new turn with the advent of sophisticated information gathering techniques. This section delves into how individual privacy is being leveraged to sway political outcomes, often without the knowledge or consent of those affected.
In the digital age, personal information serves as a potent tool for political campaigns. By analyzing vast amounts of private data, parties can tailor their messaging to resonate with specific demographics, thereby enhancing their outreach and impact. This targeted approach, however, raises significant ethical questions about the boundaries between legitimate campaign tactics and intrusive practices.
Election outcomes can be significantly influenced when parties gain access to detailed profiles of voters, including their beliefs, preferences, and social connections. Such insights enable campaigns to craft messages that are not only persuasive but also deeply personal, potentially swaying undecided voters and reinforcing the choices of those already aligned with a particular viewpoint.
The implications of this manipulation extend beyond the electoral process. Once in power, leaders and parties can continue to utilize collected data to shape policy and public opinion, maintaining their influence and control. This continuous cycle of data collection and application blurs the lines between governance and surveillance, challenging traditional notions of democracy and privacy.
Addressing these issues requires a multifaceted approach, including stricter regulations on the collection and use of personal information, enhanced transparency in political advertising, and greater public awareness about the methods and motives behind data-driven political strategies. Only through concerted efforts can the integrity of democratic processes be safeguarded against the encroachments of data-driven manipulation.
The Impact on Consumer Rights
This section delves into how the practices of information intermediaries can significantly undermine the rights of individuals. It explores the ways in which these entities, through their operations, can encroach upon fundamental freedoms and protections that consumers are entitled to.
Consumer rights are often compromised in several ways when information intermediaries are involved. Here are some key areas where these impacts are most evident:
- Right to Privacy: Individuals have the right to protect their personal information from being accessed without consent. Information intermediaries, however, often collect and distribute this sensitive information without adequate safeguards, violating this fundamental right.
- Right to Information: Consumers have the right to know how their personal information is being used and by whom. Many information intermediaries operate in opaque ways, making it difficult for individuals to track the usage of their data.
- Right to Control Personal Information: Individuals should have the ability to control who has access to their personal information and under what circumstances. This right is frequently undermined by the practices of information intermediaries, who may share data with third parties without explicit consent.
- Right to Security: There is an expectation that personal information will be protected against unauthorized access and misuse. Information intermediaries often fail to implement robust security measures, leading to breaches and unauthorized data usage.
The implications of these infringements are far-reaching, affecting not only individual privacy but also broader societal trust in digital systems and markets. It is crucial for regulatory frameworks to evolve to protect these rights effectively.
In conclusion, the activities of information intermediaries pose significant challenges to consumer rights. Addressing these issues requires a comprehensive approach that includes strengthening legal protections, enhancing transparency, and empowering consumers with better tools to manage their personal information.
Legal Loopholes Exploited by Brokers
This section delves into the various legal gaps that information intermediaries frequently exploit to their advantage. These loopholes often allow them to operate with minimal oversight and regulation, significantly impacting the security and privacy of personal information.
One of the primary ways these intermediaries leverage legal gaps is through the selective interpretation of privacy laws. Many statutes are outdated or written in ways that are open to broad interpretation, enabling these entities to collect and use personal information in ways that might not be explicitly prohibited by current legislation.
| Type of Loophole | Description | Impact |
|---|---|---|
| Outdated Regulations | Laws that do not account for modern data collection and usage practices. | Increased vulnerability of personal data. |
| Broad Interpretations | Statutes that allow for wide-ranging interpretations, often in favor of the collector. | Potential for extensive data exploitation. |
| Lack of Enforcement | Weak or non-existent mechanisms to enforce existing laws. | Minimal deterrent against illegal data practices. |
Moreover, the global nature of the internet exacerbates these issues. Information intermediaries often operate across multiple jurisdictions, each with its own set of laws and regulations. This complexity can create a legal gray area where enforcement becomes challenging, allowing these entities to exploit discrepancies between different legal systems.
Addressing these legal loopholes requires a concerted effort from policymakers, regulators, and the public. Updating and harmonizing privacy laws globally, enhancing enforcement mechanisms, and increasing public awareness about the implications of data collection are crucial steps towards mitigating these risks.
Technological Vulnerabilities Amplified
In this section, we delve into how modern technological advancements, while beneficial in many aspects, have inadvertently amplified certain vulnerabilities. These vulnerabilities can be exploited, leading to significant security breaches and privacy infringements. The integration of sophisticated systems and the vast amount of information they handle have created new avenues for potential misuse.
The complexity of current information systems has made them more susceptible to various forms of cyber-attacks. Hackers can exploit these weaknesses to gain unauthorized access to sensitive information. Moreover, the interconnectedness of these systems means that a single point of failure can have cascading effects, impacting multiple sectors and individuals.
Additionally, the rapid pace of technological innovation often outstrips the development of robust security measures. This lag results in a situation where systems are deployed with inadequate protection, making them easy targets for those with malicious intent. The challenge lies in balancing the need for innovation with the imperative to secure these advancements adequately.
Furthermore, the use of artificial intelligence and machine learning in processing and analyzing vast datasets has introduced new vulnerabilities. While these technologies enhance efficiency and accuracy, they also present new opportunities for manipulation and exploitation. Understanding and mitigating these risks is crucial for safeguarding privacy and maintaining the integrity of information systems.
In conclusion, while technology continues to propel society forward, it is essential to address and rectify these amplified vulnerabilities. By doing so, we can ensure that the benefits of technological progress are not overshadowed by the risks it entails.
Solutions to Curb Data Broker Abuses
Addressing the challenges posed by information intermediaries requires a multifaceted approach. This section explores effective strategies to mitigate the adverse effects of these entities, focusing on regulatory enhancements, technological innovations, and consumer empowerment.
Strengthening regulations is paramount. By tightening laws governing the collection, storage, and sale of personal information, governments can create a more robust framework that deters illicit practices. Mandatory transparency requirements and stricter penalties for violations can significantly reduce the likelihood of abuse.
Technological solutions also play a crucial role. Developing advanced encryption methods and anonymization techniques can protect individual privacy by making personal information less accessible to unauthorized parties. Additionally, implementing blockchain technology can enhance data integrity and traceability, making it harder for intermediaries to engage in deceptive practices.
Consumer awareness and empowerment are equally vital. Educating the public about the risks associated with information sharing and providing tools for data protection can encourage proactive behavior. Offering individuals more control over their personal data, such as the ability to easily opt out white pages-out of data collection or request deletion of their information, can significantly curb abusive practices.
Collaboration between government, technology developers, and consumer advocacy groups is essential for effective implementation of these solutions. By working together, these stakeholders can ensure that the measures taken are comprehensive and sustainable, ultimately leading to a safer digital environment for all.
